 Matthias with his trophy
Matthias with his trophy
On the 3rd of June 2023, at the X demoparty in Someren in the southern Netherlands, quiss aka Matthias Kramm presented Boo as his entry in the C64 4K Intro category. You can watch it on YouTube here. While the demo mainly featured a couple of spinning cubes, the edges of those cubes were drawn using a new algorithm he calls “Bit-Reversal Rendering”. This brought the number of CPU cycles needed to plot each pixel of a line on a Commodore 64 down from 7 to 5, reducing the overhead on a number of key graphical effects. This earned him first place, and the adoration of the assembled demosceners.
There are maybe half a dozen line plotting methods in existence and most of them date back to the cold war, so presenting a brand new one as a 4 kilobyte C64 intro that does parallel processing on the floppy disk controller is pretty cool.
Of more general interest though, is the better temporal stability of this algorithm in comparison to others, which can be seen in the above animation.
He later published details of how the algorithm works, but didn’t include an implementation. In this article I provide such an implementation, along with some further notes and explanations. I have also reproduced his animations in interactive form, and at the end I’ll show a new variation of the function I came up with.
 A line algorithm used to menace an innocent watervine farmer
A line algorithm used to menace an innocent watervine farmer
 Mole with hard hat - Stable Diffusion 2024
Mole with hard hat - Stable Diffusion 2024
 Cargo crates - Stable Diffusion 2024
Cargo crates - Stable Diffusion 2024
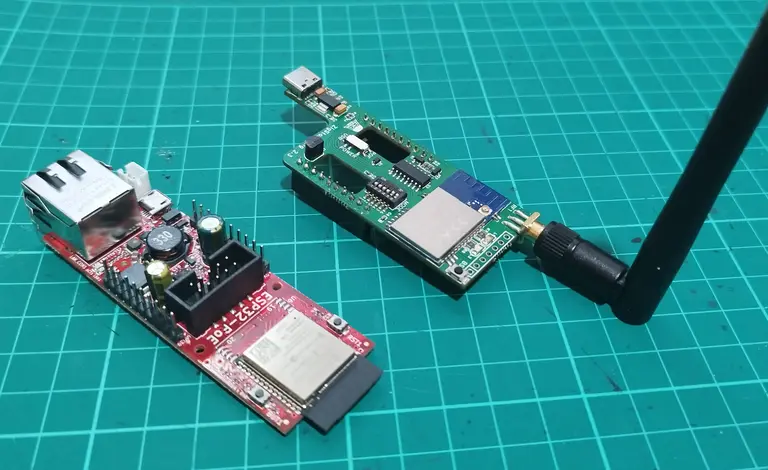 The two halves of the ZigStar OliZig POE
The two halves of the ZigStar OliZig POE